It is very common to hear the word phishing in our day-to-day life, sometimes we are even able to use it without really knowing what the meaning of this word is. The purpose of this Blog Post is to provide a deeper understanding of the most prevalent and dangerous cyber-attack technique: phishing.
Exploring the world of phishing
Phishing is a type of cyberattack designed to target individuals through emails, text messages, phone calls or other forms of communication. Its primary goal is to trick the recipient into performing actions desired by the attacker, such as revealing financial information or login credentials to corporate systems or other sensitive information.
As a form of social engineering, phishing involves psychological manipulation and deception, where threat actors pose as trusted entities to induce users to perform specific actions, such as clicking on malicious links, downloading and installing malicious files, or disclosing private information such as bank account numbers or credit card details.
What distinguishes phishing and makes it especially dangerous is that its success depends on human action. Even if advanced security measures are implemented, a simple user error can compromise an entire company.
The Impact on the Organization
Phishing attacks can have a variety of consequences, the most common of which are:
- Data loss
- Compromise of accounts and login credentials
- Ransomware and/or malware infections
- Financial losses and fraud from banking transactions
Advanced phishing strategies
As all technologies evolve, so do phishing campaigns. Attackers learn from their mistakes and improve their strategies, making them more difficult to identify. Recently, a new strategy has been discovered that we want to address in this article. It involves phishing that spoofs Meta for Business, using a Salesforce website as a bridge to direct the user to a seemingly secure target.
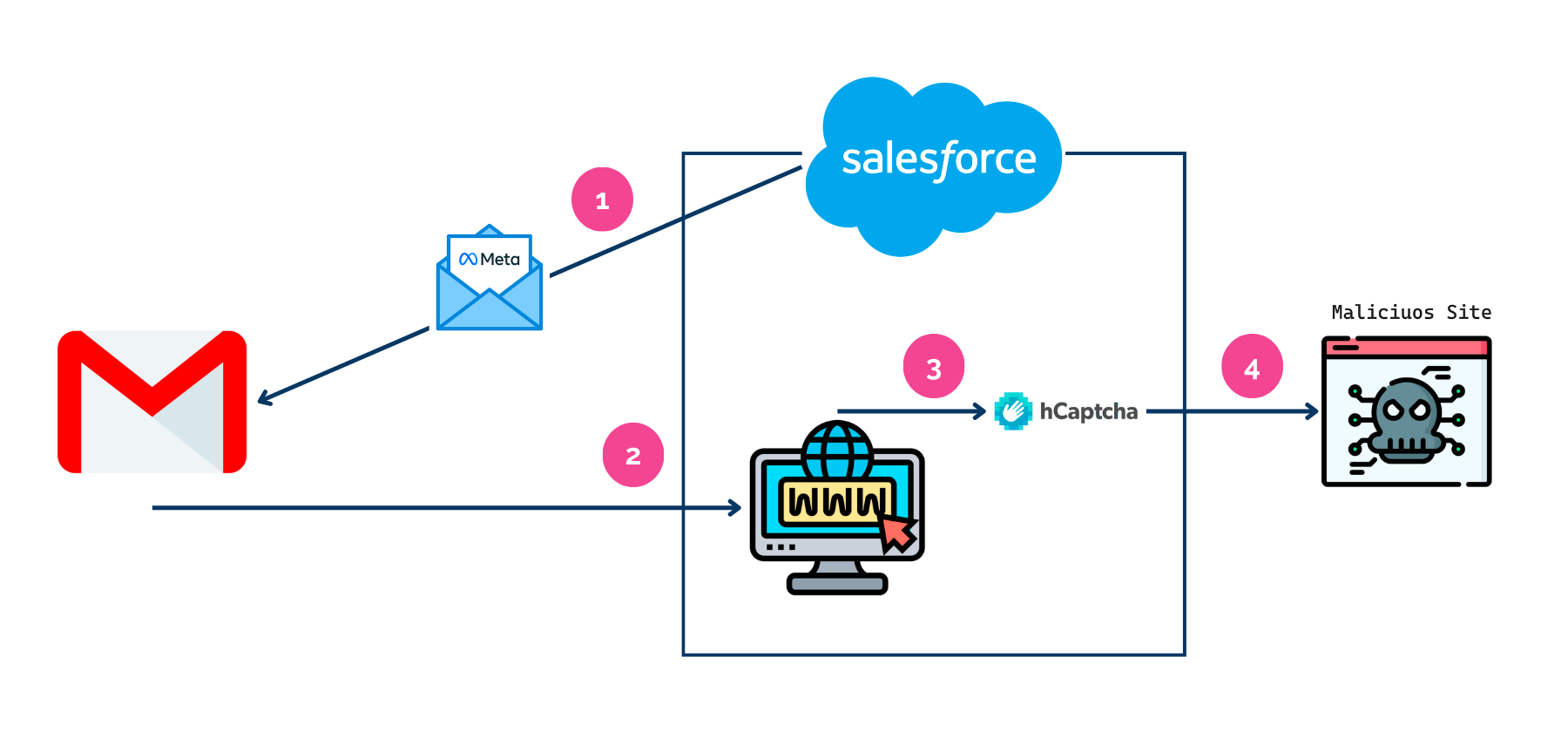 It starts with an email pretending to be from Meta for Business, informing the user of a violation of the community rules that involve account deletion (1). This type of campaign is targeted, as it addresses the user by name. Although the sender of the email is noreply@salesforce.com, which is suspicious, it is a trusted domain that avoids detection by conventional filters and generates fewer doubts in the user. The email includes a button to send an appeal.
It starts with an email pretending to be from Meta for Business, informing the user of a violation of the community rules that involve account deletion (1). This type of campaign is targeted, as it addresses the user by name. Although the sender of the email is noreply@salesforce.com, which is suspicious, it is a trusted domain that avoids detection by conventional filters and generates fewer doubts in the user. The email includes a button to send an appeal.
If the user clicks the button, he is directed to a Salesforce-hosted website (2), requesting an identity verification via hCaptcha (3). Once the verification is completed, the user is left vulnerable to the attack (4).
In this case, the page was hosted by Salesforce, but any other platform can act as a bridge. This pattern is persistent and, despite technical efforts, many sites manage to go undetected. By contacting the Salesforce team, it has been possible to remove the intermediate page and block the mailing from Salesforce.
How to identify the threat?
As we have seen, phishing is a type of attack that is characterized by its versatility, so there is no exact method to identify it. However, there are signs that will give us a clearer picture of whether the email we have in front of us is legitimate or not:
- Pay attention to the sender: Verify that the sender is consistent with the content of the email. In the case mentioned above, the email pretended to be from Meta for Business but came from a Salesforce address, a clear indicator that it was not legitimate.
- Review images and links: By hovering the mouse over images, buttons, or links, you can view the address to which they redirect. It is crucial to verify that the domain matches the owner of the client or partner. Platforms such as VirusTotal can help to check the legitimacy of domains.
- Check typography and special characters: Legitimate emails follow specific typography standards. Atypical elements may indicate a phishing attempt.
- Verify through regular channels: If the sender claims to be part of your organization, use regular communication channels to confirm their identity. The CEO fraud case is also a very common attack.
Protecting ourselves in the digital world.
In summary, phishing is a persistent threat that is continually adapting. Awareness, education, and the use of security technologies are essential to be protected. Being informed and vigilant helps build a safer and more resilient digital environment against this growing threat. In a world where cybersecurity is crucial, prevention and attention to detail are critical to avoid falling into phishing traps.





 Cookie configuration
Cookie configuration